Baserow database tokens: Secure API authentication
Baserow database tokens provide secure, permission-controlled API access without exposing your account credentials to external applications.
Database tokens are permanent API keys that let you securely connect external applications to your Baserow data. Create tokens to authenticate API requests for reading, writing, updating, and deleting data without sharing your login credentials.
Performance note: Baserow Cloud has a limit of 10 concurrent API requests to ensure fair usage across all users. Tables with fewer fields and rows process faster. Self-hosted has no rate limits.
What are database tokens?
Database tokens are permanent authentication keys that grant programmatic access to your Baserow data through the REST API. Unlike temporary session tokens, database tokens don’t expire and can be used continuously by external applications, scripts, or integrations.
These tokens act as digital keys, allowing authorized systems to perform specific operations on your databases while maintaining security through granular permission controls. You can create multiple tokens with different access levels for different use cases.
Token types in Baserow
Baserow offers two authentication methods for API access:
| Token type | Duration | Use case | Permissions | Operations |
|---|---|---|---|---|
| Database token | Permanent | External applications, automation tools, long-running scripts | Configurable per workspace and table | Create, read, update, delete rows; limited to data operations |
| JWT token | Temporary (7 mins) | Short-term operations, development testing | Full account access | All API endpoints including database/table management |
Enterprise license: Only workspace-level admins and builders can create database tokens, ensuring proper access control for sensitive operations.
Database tokens only allow reading or manipulating the data of a table. If you want to create, update or delete the structure of the table, you need a JWT token.
This token can be generated by calling https://api.baserow.io/api/redoc/#tag/User/operation/token_auth and passing the username and password of a user who has Admin or Builder rights on the table.
The token itself is added to the header in the following format Authorization: JWT <Token>
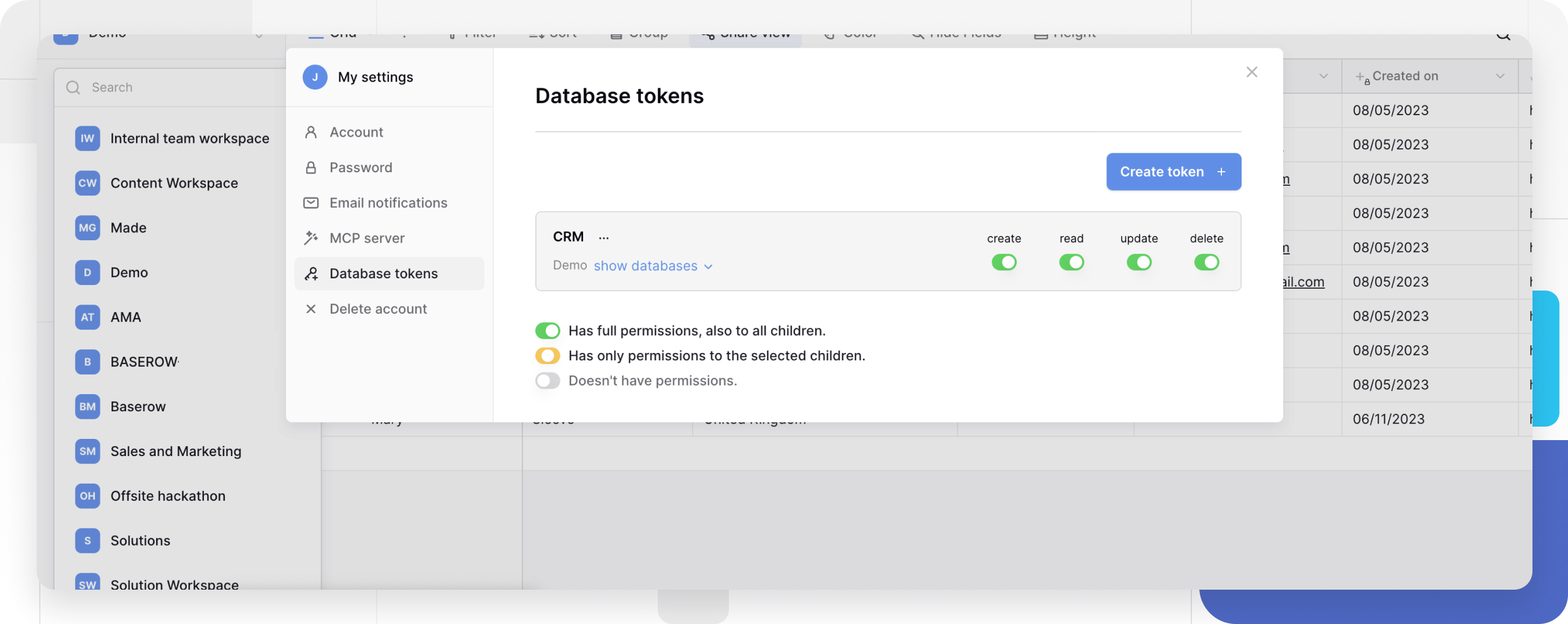
How to create a database token
-
Access token settings
- Click on your workspace in the top left corner
- Navigate to Settings
- Select the Database tokens tab
-
Create new token
- Click Create token +
- Use a descriptive name that indicates the token’s purpose (e.g., “Zapier Integration” or “Mobile App Access”)
- Select the target workspace
-
Generate and secure your token
- Click Create token
- Copy the generated token immediately
- Store it securely
To connect Power BI to Baserow, you need to construct the correct API endpoint URL. This section explains how to find and format these URLs.
Managing database tokens
It is recommended to create separate tokens for different applications or environments. Document where each token is used for easier management.
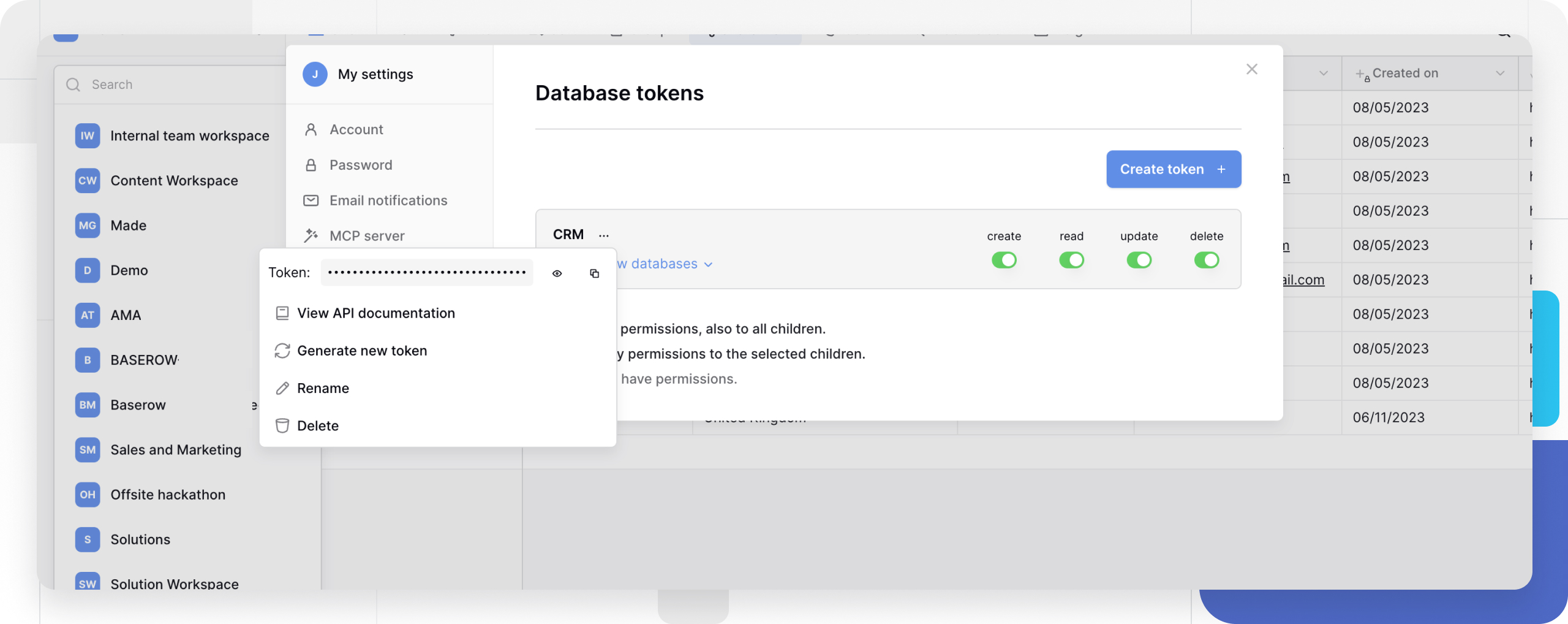
Copy an existing token
- Find your token in the Database tokens list
- Click the ellipsis (•••) menu beside the token
- Click the copy icon to copy the token ID
Regenerate a compromised token
If your token is accidentally exposed:
- Click Generate new token on the existing token
- Update all applications using the old token
- The old token becomes invalid immediately
Delete unused tokens
- Click the ellipsis menu beside the token
- Select Delete to permanently remove access
- Ensure no applications are still using the token
Rename tokens
Click Rename to update the token’s display name without affecting its functionality.
Database token permissions
Database tokens use role-based permissions that determine what operations are allowed:
| Permission | Description | API Operations |
|---|---|---|
| Create | Add new rows (includes read access) | POST to /api/database/rows/table/{table_id}/ |
| Read | View existing data | GET from rows and table endpoints |
| Update | Modify existing rows (includes read access) | PATCH to row endpoints |
| Delete | Remove rows | DELETE from row endpoints |
No access: Token cannot interact with table
Only grant necessary permissions, review token permissions periodically, and use different tokens for development/production.
Setting workspace-level permissions
- All tables checked: Token works on every table in the workspace
- Specific tables: Limit access to selected tables only
- Operation toggles: Enable/disable create, read, update, delete per workspace
Using tokens with the API
Authentication header format
Authorization: Token YOUR_DATABASE_TOKEN_HERE
Example API request
curl -H "Authorization: Token abc123def456" \
-H "Content-Type: application/json" \
https://api.baserow.io/api/database/1/tables/2/rows/
Common integration patterns
- Zapier/Make: Use token in connection settings
- Custom scripts: Include in HTTP headers
- Mobile apps: Store securely, never hardcode
Frequently asked questions
What happens if I delete a token that’s in use?
Applications using the deleted token will immediately lose access and receive authentication errors. Update applications with a new token before deleting the old one.
Can I see what operations a token has performed?
Currently, Baserow doesn’t provide detailed audit logs for token usage. Consider implementing logging in your applications that use the tokens.
How do I know if my token permissions are correct?
Test your token with a simple API call to verify permissions work as expected. The API will return permission errors for unauthorized operations.
What’s the difference between database tokens and personal API tokens?
These are the same thing - “database tokens” and “personal API tokens” refer to the same permanent authentication method in Baserow.
Can I use the same token for multiple workspaces?
No, each database token is scoped to a single workspace. Database tokens authenticate you across all databases in the selected workspace you have access to. One token can interact with databases in the specified workspace where you’re a member, subject to your permissions in each workspace. Create separate tokens for accessing different workspaces.
Troubleshooting common issues
Authentication errors
- Verify token is included in the
Authorizationheader - Check token hasn’t been deleted or regenerated
- Ensure proper header format:
Authorization: Token YOUR_TOKEN
Permission denied errors
- Review token permissions for the target table
- Confirm workspace access is enabled
- Check if you’re trying operations beyond token scope
Token not working after creation
- Copy the token immediately after creation
- Tokens cannot be viewed again once the creation dialog closes
- Regenerate if you suspect the token was copied incorrectly
Related content
- Baserow webhooks - Real-time notifications for data changes
- Database API documentation - Complete API reference
- Database and table IDs - Finding required identifiers
- Zapier integration - Connect with 4000+ apps
- Make integration - Advanced automation workflows
- Backend API - Technical API documentation
- How to connect Baserow to external tools with the API
Still need help? If you’re looking for something else, please feel free to make recommendations or ask us questions; we’re ready to assist you.
-
Contact support for questions about Baserow or help with your account